Introduction to SSL
The SSL protocol was originally developed by Netscape for Web browsers. SSL is a set of rules governing authentication and encrypted communication between clients and servers. SSL is widely used on the Internet by an increasing number of varied applications, especially for interactions that involve exchanging confidential information such as credit card numbers. SSL evolved into the Transport Layer Security (TLS) Version 1 standard.
SSL is positioned as a protocol layer between the Transmission Control Protocol (TCP) layer and the application to form a secure connection between clients and servers so that they can communicate in a secure manner over a network by providing:
- Privacy, where data messages are encrypted so that only the two application endpoints understand the data.
- Integrity, where message digests detect if any data was altered in flight.
- Authentication, which verifies the identity of the remote node, application, or user by using digital certificates.
Figure 1 shows an example of a TCP/IP network using SSL.
Figure 1. TCP/IP network using SSL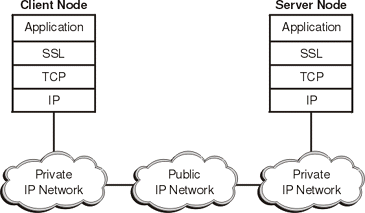
This type of secure connection ensures that all data exchanged between clients and servers is encrypted, and is therefore not readable by a third party on the Internet. SSL has gained popularity in the Internet industry primarily because of its use of public-key certificates as a means of authenticating principles.To establish the connection, SSL requires, at a minimum, a server certificate. As part of the initial SSL handshake process, the server presents its certificate to the client to authenticate the server's identity. The authentication process uses public-key encryption and digital signatures to confirm that the server is, in fact, who the server claims to be (that is, the server's certificate is valid).Once the server has been authenticated (that is, the client determines that the server's certificate is valid), the client and server use techniques of public-key encryption to exchange a symmetric key, which is then used to encrypt all the information exchanged for the remainder of the SSL session. Message digests are used to detect data tampering. A different key is created for each client and server connection. As a result, if unauthorized users intercept and decrypt a session key (which is unlikely), they cannot use it to monitor later SSL sessions.



























